Predictability with Precision
Leverage the power of predictability with end-to-end IT, cybersecurity, and compliance solutions. Trust your information with dependable IT services, managed by industry-leading experts who stay one step ahead of threats, safeguarding you from risks. Our solutions ensure protection against data breaches, system failures, and compliance issues, strengthening your organization's reputation today and securing your business for tomorrow.

Uzado integrates all service pillars for your business...
Challenges
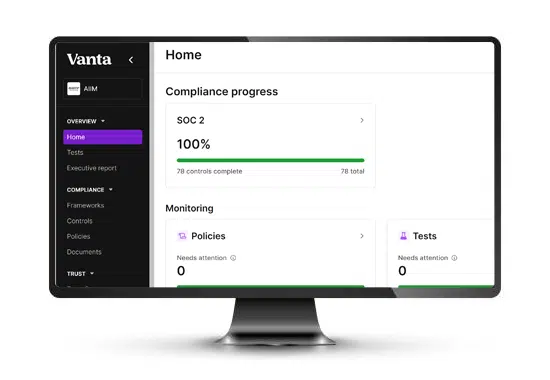
Compliance
Protecting against liabilities & preparing for audits isn’t easy, yet enables business growth.
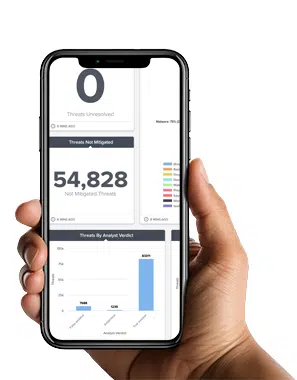
Protection
Managing risk across a growing threat landscape 24×7 is time consuming & required expertise.
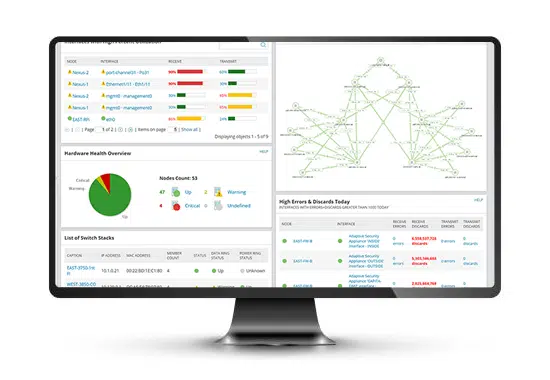
Visiblity
Monitoring a dynamic patchwork of siloed systems manually inst’t scalable. A single pane of glass is ideal.
Expertise
Identifying, mitigating, & managing threats requires experts that are in short supply.
Operations
Automating security alerts & processes frees up DevOps to get back to building valuable code.
Solutions
- Managed SIEM
- Managed EDR / XDR
- Vulnerability Management
- Phishing and Security Awareness
- Managed Governance, Risk and Compliance

- Physical / Virtual (Windows, Linux)
- Proactive Patch Management
- Managed and Monitored Firewalls
- Managed Network and Cloud Services (Azure, AWS, GCS)
- Compliance and Security Implementation
- ISO 27001, SOC2 Type 1 & Type 2, PCI, DSS, GDPR, NIST
- Pen Testing
- Threat Risk Analysis
- Security Architecture review
Benefits

Digital Architects: Building Tomorrow's Technology Today
Uzado keeps up with the ever-changing digital landscape by innovating secure, cutting-edge solutions to help you build a secure digital future. |
Service Catalog
| Service | Service Type | Delivery Dept | Description |
|---|---|---|---|
| Vulnerability and Patch Management | Managed | SecOps / ITOps | Identify, categorize, prioritize, and resolve vulnerabilities in your environment with recommendations on remediation. Options for Weekly/Monthly/Quarterly scans and reporting. |
| Vulnerability Management – PCI | Managed | SecOps / ITOps | Perform quarterly ASV scans of PCI environments. |
| MDR (Managed detection and response) | Managed | SecOps | Using Uzado’s EDR technology, Uzado will monitor and manage the EDR solution alerting and investigating of threats in a client environment leveraging Uzado’s tech stack. |
| Uzado XDR | Managed | SecOps | A combination of SIEM security monitoring, alert notification and EDR management, Uzado’s technical stack will manage and correlate threats and alert in order to provide maximum visibility and response through correlation of SIEM and EDR alerts. |
| SIEM Security Monitoring and Alerting | Managed | SecOps | Managing SIEM security monitoring and alerting. Uzado will manage SIEM alerting services which include an alert framework, and investigation of threats in a client environment. |
| Managed Phishing & Security Awareness Training | Managed | SecOps | Leveraging the KnowBe4 Platform, Uzado will ensure the right content is targeted to the right user group. Includes monthly reporting on success/failure metrics and trend reporting. |
| Incident Response | Managed | SecOps | Operating in support of a your Computer Incident Response Team (CIRT) we can respond to security breaches, viruses, and other potentially catastrophic incidents in enterprise environments. Specifically supporting the technical role of Incident Response guidance and forensics. |
| IT/Network Management | Managed | ITOps | Managing IT resources and technology (Cloud & on-prem), Uzado can assist with day to day operations and support of clients day to day operation of enterprise technology supporting all aspects of operational IT |
| Helpdesk | Managed | ITOps | Manage end user requests in the day to day support of a clients operation |
| MGRC (Managed Governance, Risk and Compliance) | Managed | Professional Services | SOC 2 Type 1 & 2, ISO27001, PCI, GDPR, NIST Program support, validation and alignment (includes GRC Tooling) |
| Compliance Implementation (ISO/NIST/SOC 2/PCI) | Professional Service | Professional Services | Program design, build and implementation, audit and certification (applicable) |
| Compliance / Security Gap Assessment (ISO/NIST/SOC 2/PCI) | Professional Service | Professional Services | Compliance / Security Gap Analysis + Remediation Road mapping |
| Vulnerability Assessment | Professional Service | Professional Services | Identify, categorize, prioritize, and resolve vulnerability’s in your environment with recommendations provided. This is the same as Vulnerability Management, but a stand alone, single scan service |
| Penetration Test | Professional Service | Professional Services | Identify vulnerabilities in your environment, and also determine what the impact would be if an attacker exploited those vulnerabilities using the Penetration Testing Execution Standards (PTES). This tests any protective technical controls in place. |
| Network Architecture and Implementation | Professional Service | Professional Services | Design and implementation of properly segmented network including the configuration and implementation of network technologies / IAM solutions. |
| Cloud Services | Professional Service | Professional Services | Migrate your on-prem legacy assets to the cloud |
| Cloud Services | Technology | Private/Public Cloud | Host your critical applications |























